Row-level permissions
Target database: Snowflake, Databricks SQL, Google BigQuery, Azure SQL Database, Azure Synapse SQL, Amazon Redshift
Row-level permissions are used to manage data access policies on entities in the target database. Available grantees (roles) and row-level policy definitions are managed in CONFIG_ENTITY_PERMISSIONS.
See also:
Usage
Select a Row-level policy for the entity under Permissions tab and select the ROLEs to be attached to the policy, in case target database requires this information.
Notes
Check Export SQL/Entity SQL after defining permissions to see generated DDL.
Configuration
Precondition
Row level policies with their attributes have to be defined in CONFIG_ENTITY_PERMISSIONS before they can be used here. Some databases require also Grantees to be defined beforehand.
Configuration of Row-level permissions explains the setup for supported target databases
Row-level permission handling
Row-level permissions can be given, modified (only the grantee list if being required) and deleted for an entity under the Permissions-tab in Row level permissions - section.
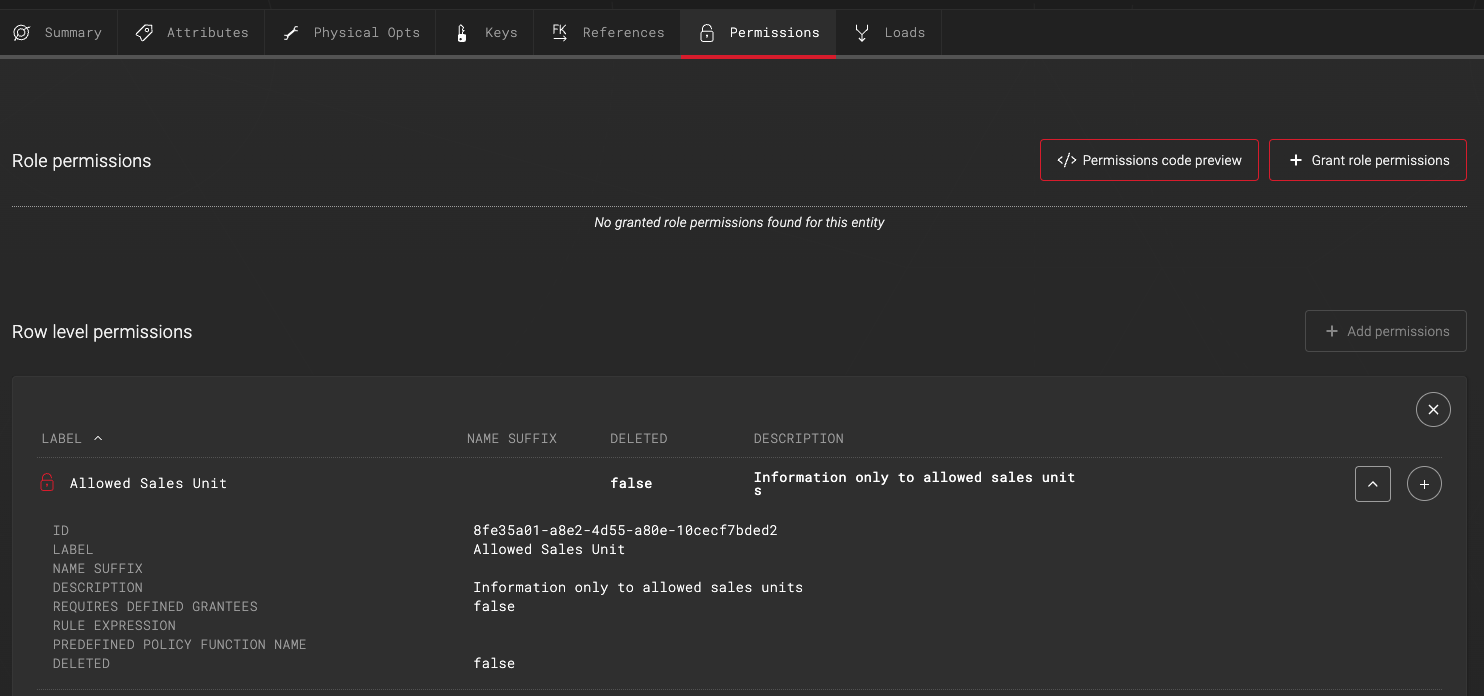
Row level permissions available will be browsable under the row level permissions section. To attach the row level permission to the entity one needs to click on the plus-sign.
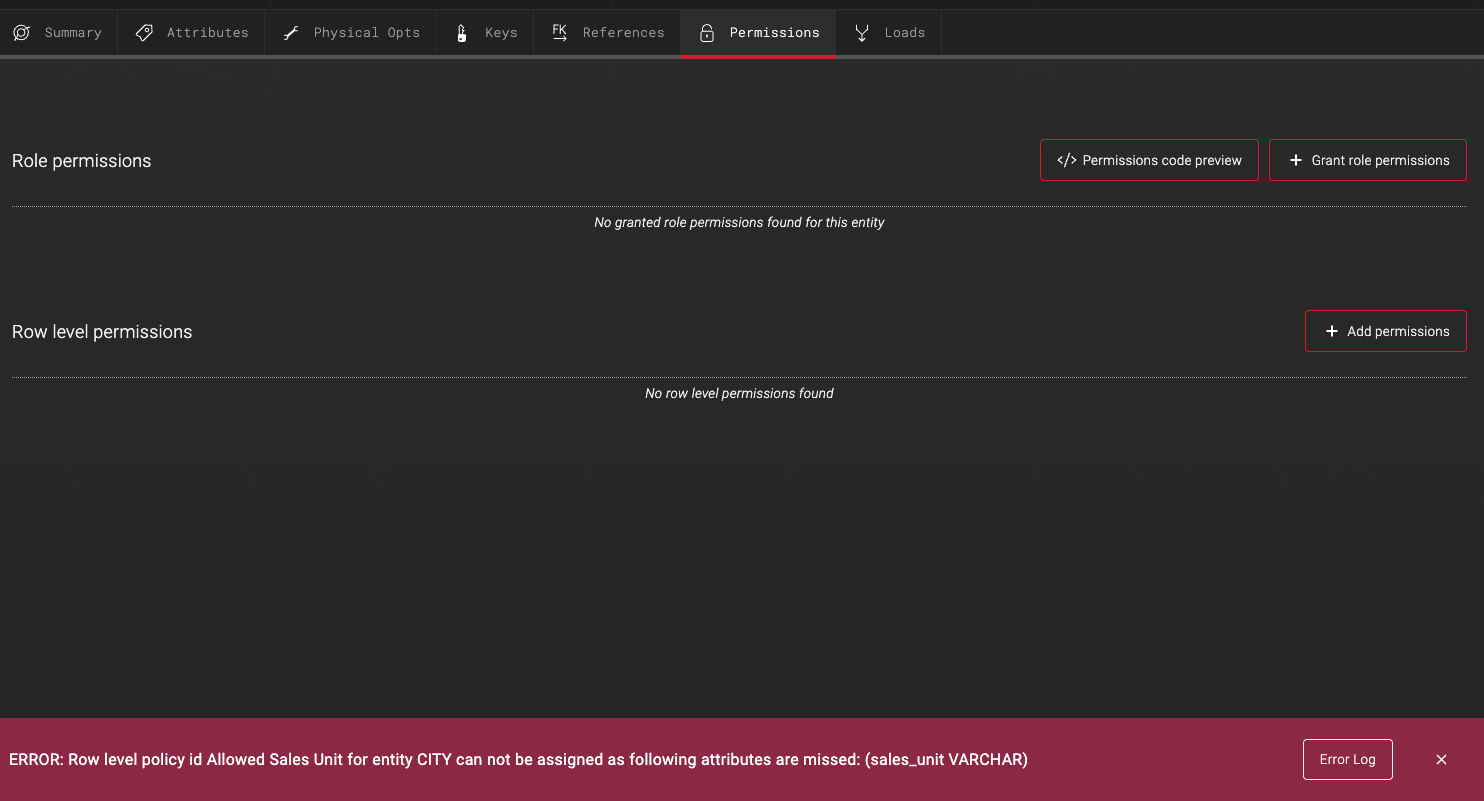
In case the entity does not have matching attributes with the row level permission, an error will be given
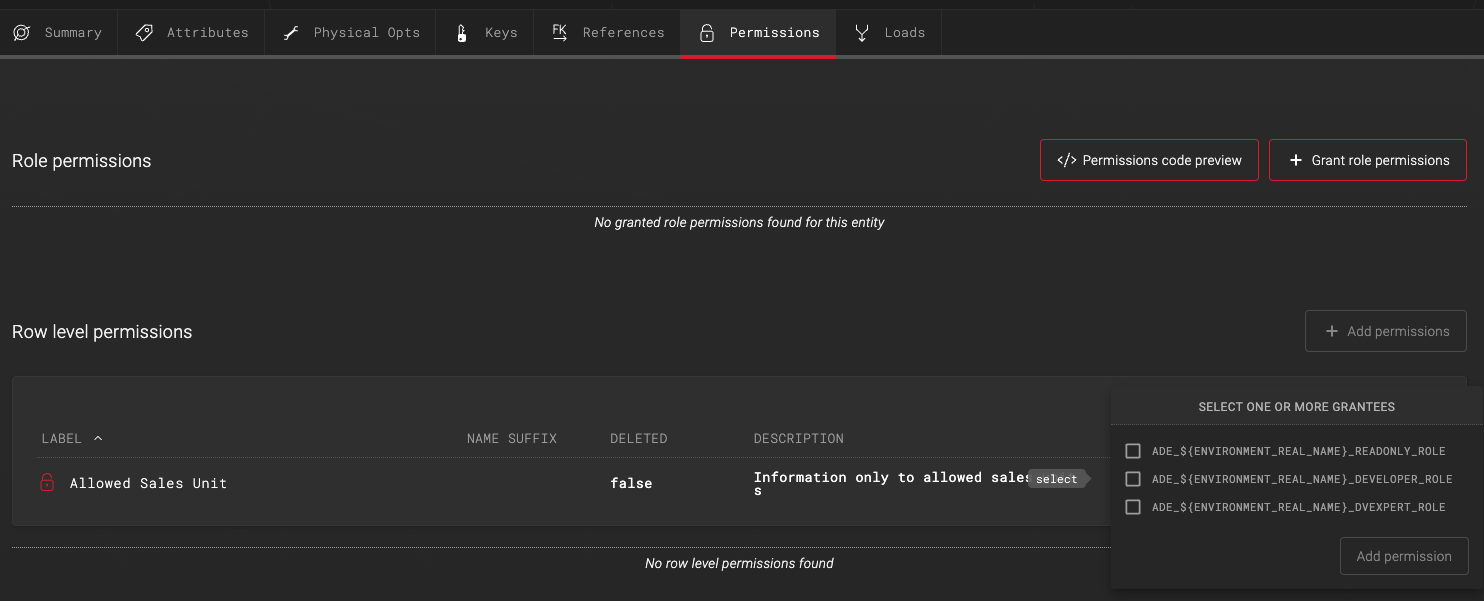
If row level permission is set to require grantees, they will be requested to be chosen during the row level permission addition
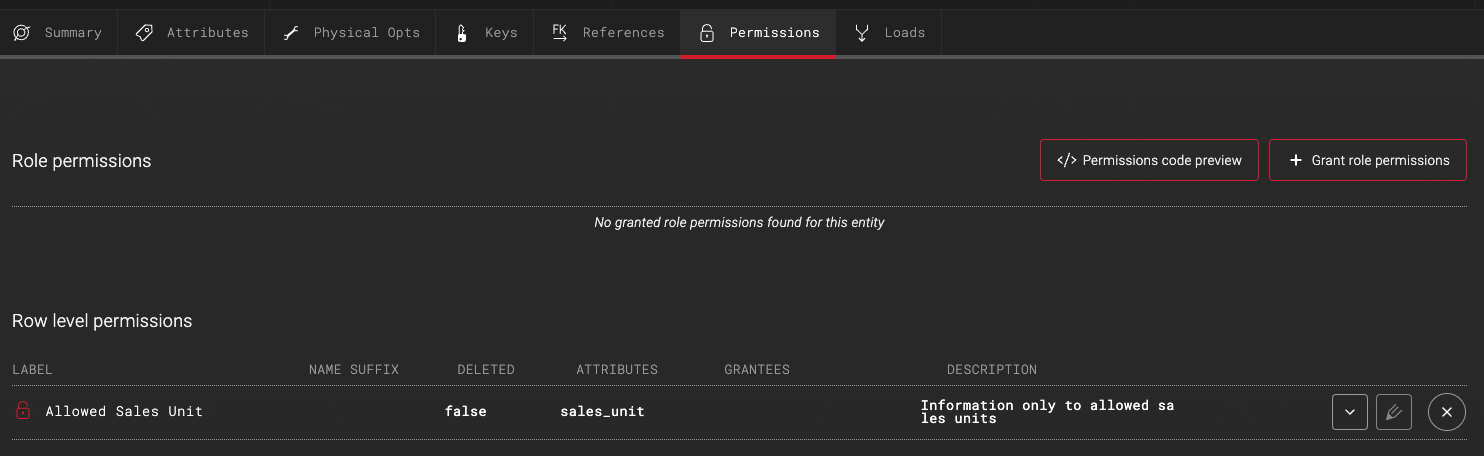
When row level permission passes the validation, it will be attached to the entity and is shown as a removable row level permission
One can verify the behaviour by clicking the Permissions code preview- button.
One can only modify the given grantee list, in case row-level permission requires such.
Row level permission can be removed from the x-button.
